Main Article Content
Abstract
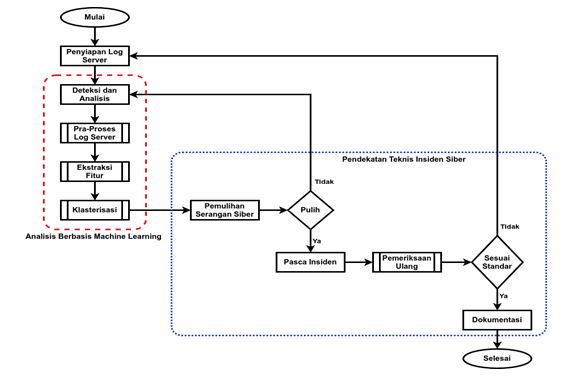
Based on the OWASP Top Ten document in 2021, attacks or vulnerabilities in an application in the form of injection still rank in the top 3. SQL Injection attacks are still classified as injection vulnerabilities so they need special attention from Information & Communication Technology Managers. Badan Siber dan Sandi Negara (BSSN) has published a document related to preventing SQL Injection attacks. However, the document has not included a cyber attack analysis process that uses the K-Means clustering approach. So in this research, a collaborative method of handling cyber attacks in the form of SQL Injection is proposed using the NIST SP 800-61R2 framework as a fundamental for handling cyber attacks and K-Means clustering. Before analyzing cyber attacks, it is better to use a framework or standardization that applies globally. Based on the research conducted, the K-Means clustering algorithm can help cybersecurity analysts in the process of analyzing cyber attacks that occur. The result of this research is that the optimal value is obtained that cyber attacks in the form of SQL Injection, namely 3 clusters. The hope of the research can facilitate cybersecurity analysts in analyzing cyber attacks that are poured into reports to parties in need
Keywords
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.
References
- OWASP, “The Ten Most Critical Web Application Security Risks,” The Open Web Application Security Project (OWASP), 2017.
- B. Glas, A. van der Stock, T. Gigler, dan N. Smithline, “OWASP Top 10 2021,” OWASP Project, 2021.
- Badan Siber dan Sandi Negara, “Mengenal Sql Injection dan Cara Mencegahnya,” Badan Siber dan Sandi Negara, Jakarta, 2019.
- R. Andriani, E. S. Pramukantoro, dan M. Data, “Pengembangan Sistem Visualisasi Access Log untuk Mengetahui Informasi Aktivitas Pengunjung pada Sebuah Website,” Jurnal Pengembangan Teknologi Informasi dan Ilmu Komputer, vol. 2, no. 6, hlm. 2104–2112, 2018.
- S. H. N. Harip, I. R. A. Hamid, N. Murli, dan N. Hassan, “Classification of SQL injection attack using K-Means clustering algorithm,” dipresentasikan pada International Conference on Applied Science And Technology, Kuala Lumpur, Malaysia, 2022, hlm. 040004. doi: 10.1063/5.0104348.
- I. S. Crespo-Martínez, A. Campazas-Vega, Á. M. Guerrero-Higueras, V. Riego-DelCastillo, C. Álvarez-Aparicio, dan C. Fernández-Llamas, “SQL injection attack detection in network flow data,” Computers & Security, vol. 127, hlm. 103093, Apr 2023, doi: 10.1016/j.cose.2023.103093.
- P. Cichonski, T. Millar, T. Grance, dan K. Scarfone, “NIST Special Publication 800-61 Revision 2: Computer Security Incident Handling Guide Recommendations,” 2012. doi: 10.6028/NIST.SP.800-61r2.
- A. D. Djayali, “Analisa Serangan SQL Injection pada Server pengisian Kartu Rencana Studi (KRS) Online,” Jurnal Ilmiah Manajemen Informatika & Komputer, vol. 1, no. 1, hlm. 16–24, 2020.
- M. Zulfadhilah, Y. Prayudi, dan I. Riadi, “Cyber Profiling using Log Analysis and K-Means Clustering A Case Study Higher Education in Indonesia,” International Journal of Advanced Computer Science and Applications, vol. 7, no. 7, hlm. 430–435, 2016.
- R. Gelar Guntara, “Pemanfaatan Google Colab Untuk Aplikasi Pendeteksian Masker Wajah Menggunakan Algoritma Deep Learning YOLOv7,” JTEKSIS, vol. 5, no. 1, hlm. 55–60, Feb 2023, doi: 10.47233/jteksis.v5i1.750.
- A. Handa, R. Negi, dan S. K. Shukla, Implementing Enterprise Cybersecurity with Open-Source Software and Standard Architecture. River Publishers, 2021.
- R. Ramadhan, Y. A. Sari, dan P. P. Adikara, “Perbandingan Pembobotan Term Frequency-Inverse Document Frequency dan Term Frequency-Relevance Frequency terhadap Fitur N-Gram pada Analisis Sentimen,” Jurnal Pengembangan Teknologi Informasi dan Ilmu Komputer, vol. 5, no. 11, hlm. 5075–5079, 2021.
- A. Lahitani, U. S. Aesyi, N. Wulandari, dan B. D. Santosa, “Cosine Similarity untuk Mengukur Tingkat Kesadaran pada Topik Software Security Berbasis Teks Komentar di Media Sosial Youtube,” JSI, vol. 8, no. 2, Des 2022, doi: 10.34128/jsi.v8i2.535.
- S. M. Fani, R. Santoso, dan S. Suparti, “Penerapan Text Mining untuk Melakukan Clustering Data Tweet Akun Blibli Pada Media Sosial Twitter Menggunakan K-Means Clustering,” Jurnal Gaussian, vol. 10, no. 4, hlm. 583–593, Des 2021, doi: 10.14710/j.gauss.10.4.583-593.
- S. Handoko, F. Fauziah, dan E. T. E. Handayani, “Implementasi Data Mining Untuk Menentukan Tingkat Penjualan Paket Data Telkomsel Menggunakan Metode K-Means Clustering,” tekno, vol. 25, no. 1, hlm. 76–88, 2020, doi: 10.35760/tr.2020.v25i1.2677.
- R. Ananda dan Achmad Zaki Yamani, “Penentuan Centroid Awal K-means pada proses Clustering Data Evaluasi Pengajaran Dosen,” RESTI, vol. 4, no. 3, hlm. 544–550, Jun 2020, doi: 10.29207/resti.v4i3.1896.
- S. Chowdhury, A. Nandi, M. Ahmad, A. Jain, dan M. Pawar, “A Comprehensive Survey for Detection and Prevention of SQL Injection,” 2021 7th International Conference on Advanced Computing and Communication Systems, ICACCS 2021, hlm. 434–437, 2021, doi: 10.1109/ICACCS51430.2021.9442012.
- J. Hu, W. Zhao, dan Y. Cui, “A Survey on SQL Injection Attacks, Detection and Prevention,” PervasiveHealth: Pervasive Computing Technologies for Healthcare, hlm. 483–488, 2020, doi: 10.1145/3383972.3384028.
- A. M. Al Hilmi dan E. Khujaemah, “Network Security Monitoring With Intrusion Detection System,” Jurnal Teknik Informatika (JUTIF), vol. 3, no. 2, hlm. 249–253, 2022, doi: 10.20884/1.jutif.2022.3.2.117.
- D. Hariyadi, M. Kusuma, A. Sholeh, dan Fazlurrahman, “Digital Forensics Investigation on Xiaomi Smart Router Using SNI ISO/IEC 27037:2014 and NIST SP 800-86 Framework,” dalam Proceedings of the International Conference on Science and Engineering (ICSE-UIN-SUKA 2021), Yogyakarta, 2021. doi: 10.2991/aer.k.211222.023.
- W. N. I. Al-Obaydy, H. A. Hashim, Y. A. Najm, dan A. A. Jalal, “Document classification using term frequency-inverse document frequency and K-means clustering,” IJEECS, vol. 27, no. 3, hlm. 1517, Sep 2022, doi: 10.11591/ijeecs.v27.i3.pp1517-1524.
- L. Wirz, R. Tanthanathewin, A. Ketphet, dan S. Fugkeaw, “Design and Development of A Cloud-Based IDS using Apache Kafka and Spark Streaming,” dalam 2022 19th International Joint Conference on Computer Science and Software Engineering (JCSSE), Bangkok, Thailand: IEEE, Jun 2022, hlm. 1–6. doi: 10.1109/JCSSE54890.2022.9836264.